Quantifying the assessment of security risk in your Enterprise architecture
- Oct 9, 2013
- 4 min read

The question of what is the level of security risk to your architecture? Often arises in conferences I attend. It’s a great point to raise as the identification and quantification of risks is often uncertain and descends into a qualitative judgement of areas of protection. I have caveat this with the word cloud as the extension of risk now is beyond the four walls of the enterprise into BYOx devices, external provider cloud platforms and the myriad of data on networks and databases.
Rather worryingly I often see senior CIOs not able to articulate the level of IT risk to their board which is a cause for concern in the resulting tactical firefighting that may ensure. Your assessment of risk from the context of the cost and quality of service performance in the organization must also identify mitigation and management needs that span the control of IT and business inside and outside of the enterprise.
Typical technology answers to get “ticks in the box” are addressed by high availability and disaster recovery planning and actions to check and contain security access with security tools on your data encryption, applications and network traffic. However this is only 50% of the answer in tactical actions. What is also needed is technically qualified directed activity involving technology strategic planning and investment to drive how you can leverage technology to control and improve business performance and growth. The following example graphic illustrates the span of issues at stake.
Risk Management
Degree of internal and external risk management practices and compliance.
What and how much does the cloud provider assure?
Risk Awareness
Degree of internal and external awareness and education and practices in cloud risk awareness.
Risk Impact severity
Degree of internal and external types of cloud security failure severity.
Risk impact probability
Degree of internal external types of cloud security failure impact.
Information security level requirements
Degree of security risk of data management in cloud
Degree of collaboration
Degree of internal and external dependencies of private versus public cloud.
Corporate reward
Degree of exposure and severity to corporate reputation and other risk from Cloud failure
Degree of risk reward return in the use of cloud and its trade-off.
Developing planning to address these issues are a matter of consumer and provider choices. The area of business and technology risk is well covered both in industry and governmental circles in both cyber threats, green sustainability plans as well as national and international legal challenges over intellectual property and trading competition. Technological risk management and certifications are also well-developed by international standards bodies and in analyst and technical solutions markets where many security tools and services are available. Yet even in bring these things together into a coherent digital security plan is still challenging in being sure the door is closed on IT performance risk and security. Defining the key protection points in your security and risk strategy is key and having the ability to implement it and the skills to know where parts of this are dependent and liable through 3rd party services is increasingly critical.
In a recent white paper published by Cloud Computing Work Group in The Open Group (http://www.opengroup.org/). We focused on this issue within the wider context of measuring business performance using cloud technology (https://www2.opengroup.org/ogsys/catalog/G136). We examined over 11 types of business performance including the aspects of measuring legal, contract and service delivery performance. The paper also focused on cyber security measure and proposed some metrics of performance I list here as an extract from that paper.
IT Security metrics examples
Isolation – Data Tenancy
Isolation – sovereignty
Federated Identity
Encrypted certification level
Trust policy control efficiency
Standards compliance
Audit capability efficiency
ISOLATION – DATA TENANCY
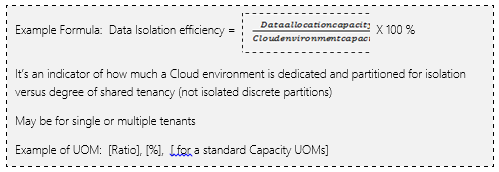
Ability to isolate single or multiple consumers’ data at different levels of isolation.
These may be by user, by service, by end point, by access, by environment, by network domain for example. It is an indication of data allocation efficiency and fidelity of the service.
It is an indicator of privacy but not necessarily if this is encrypted, secure, recoverable, backed up data (See other metrics)
This service can by physical, virtual or a hybrid of both physical and virtual partitioning
ISOLATION – SOVEREIGNTY
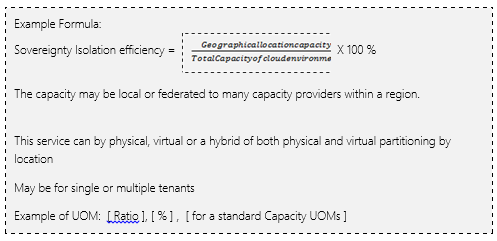
Ability to support single or multiple geographic domains
It is a measure of spread and regional support and scalability of a service
Certification of a region to support the sovereignty
Ability of a service to scale to single or multiple regions
FEDERATED IDENTITY

Ability if a Cloud service to support Identity federation.
Degree of SSO Single Sign-on efficiency to access one or many Cloud services.
ENCRYPTED CERTIFICATION LEVEL
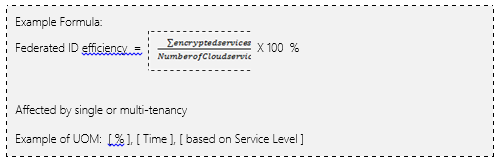
Number of encrypted services
By type and level of encryption
TRUST POLICY CONTROL EFFICIENCY

The level of single and multiple domains a policy for security is applied to.
Is an indicator of shared trust domains, open or close domain status
STANDARDS COMPLIANCE

For example HIPPA compliance that affect a Cloud service. A measure of the degree of compliance of a Cloud environment
AUDIT CAPABILITY EFFICIENCY

Degree of measurable transparency
The level of closed and open log keeping and reporting
An indicator of audit logs and tracking availability and reporting.



























Comments